Cloud computing is profitable, expandable, advantageous, and lets the users work with one another in an efficient way. Users can store confidential data on the cloud database and use it anywhere and anytime. However, both the accumulated data and the cloud-based applications need complete management of security to stop breaches.
Accredit the users who have a connection with the network: The data stored in the cloud is completely protected. When you provide access to every random user, then the data can be breached. It is always better to accredit the users who are supposed to access data on the cloud. It is better to keep logs for every users you authorized to prevent unauthorized access, thereby keeping the data safe. You can either use cloud-based free VAT software or a paid accounting application. Whatever you use, a verification can help you keep protected from different types of breaches.
Compose user-specific admission consent: When providing network access to every user, you must also frame the admittance permission depending on their job specification. Such an act will help in the reduction of the breach of data. The experts providing Management Assignment Help have a thorough knowledge of this domain.
Authorize all the software which runs on the system: Many organizations fail to realize that the software can be responsible for the breach of data located in the cloud database. Most cloud-based software is run by a third party; therefore, you must ensure that it does not pose any threat to your cloud database. The software patches must be authorized by the providers of the cloud. At the same time, administer the security patches with toughness. Blackouts of service generally happen because of configuration mistakes. If you do not know how to do this, you may hire a software or web developer.
Keep an eye on all the unethical activities: You must ensure that the data stored within the cloud and the applications unified into the cloud service remains safe. You can also install an intruder detection technology that will make you cautious there is suspicious activity in progress.
Centralize the agreement requesting procedure: You must centralize the procedure so that you can ensure that all the appeals for authorization to permit admittance of the data or applications are taking a smooth course of action. Until and unless you assign the requesting procedure, you make an error that lets criminals breach the security of your network. You can either share the system with a third party or have provided authorization to the employees working with the company then a centralized requesting procedure can help you manage a secure network. Within the process of centralization, you must permit the uploading of data to the cloud.
Provide encryption to your data for security: After your developer encrypt, then the data is secured. Always remember to encrypt your data before uploading it to the cloud. The keys to encryption and decoding the information must lie with you. As cloud services are generally provided by a third party, it is always better to keep the data protected. At the same time, when the keys for encryption and decoding lie with you, then none can use the data without your permission.
Keep an eye on the activities of a user and evaluate them for impulsive behavior: Most organizations fail to understand that the breaches to the data are done by an employee working with the company. It is not possible for an outsider to steal the data from the network without help from an employee. Most times, the authorities fail to recognize the masterminds behind the breach of data. When you keep an eye on the activities of the users, then you can prevent the data from being stolen. If you find any employee getting involved in any suspicious activity, then you must question them regarding it.
The cloud service providers are responsible for keeping an eye on suspicious activity within the network. If you do that on behalf of them, then your data remains safe and protected. At the same time, you can prevent any unexpected episode. If you manage to see any suspicious activity within the network, notify the service providers immediately and ask them to take care of it.
An agreement is usually signed between the service provider and the customer, which protects the interest of the customers. It is always suggested that you must keep an eye on the network and report if any suspicious activity takes place. At the same time, you must also know that cloud computing provides a lot of benefits, but it also brings you a lot of security threats. Such tips can keep your data protected and safe.
In need of developers? Here’s where you can find the best pool of tech talents. With Cloud Employee, you can hire dedicated offshore developers across many technologies. Talk to us, learn more how Cloud Employee works, or see our Developer Pricing Guide.
Author’s Bio
Apart from being a blogger, John Mathew is a software engineer by profession. He is a reputed expert who is known for his Xero Accounting Assignment Help services to students coming from different parts of the world.
Hire A Developer Now!
Featured Article

How to Become a High-Performing Developer

CSS grid vs. Flexbox: which to use when?
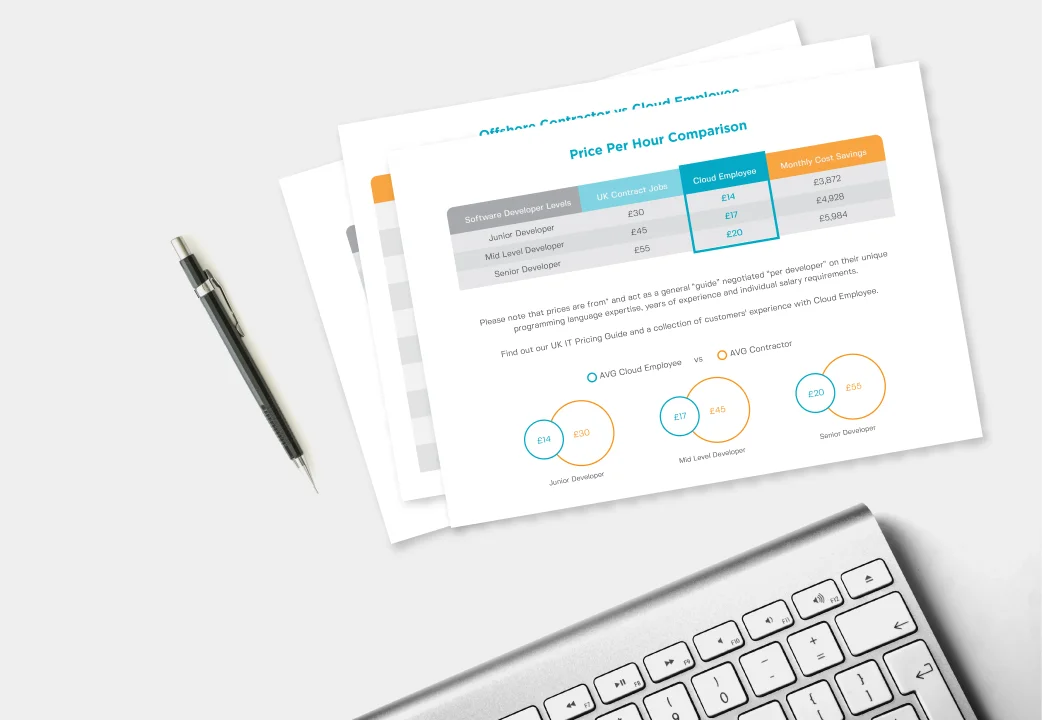
Download Our Developer Pricing Guide
We did an analysis on the difference between western and Philippines developer salaries. Uk, USA and Australia pricing comparisons available.
Download